Cyber security - News
Cellebrite, a pioneer in AI-powered Digital Investigative and Intelligence solutions for the public and private sectors, announces it has substantially expanded its capabilities through the acquisition of Corellium, a pioneer in Arm-based virtualization software. The addition of Corellium's technology and world-class technical talent further strengthens Cellebrite's market and technology leadership. Dramatically accelerating time This combination creates the industry's most complete digital...
Magenta Security Services marked its 30th anniversary in style last night at the Security & Fire Excellence Awards, where the company was named Security & Fire Sustainability Champion for the third year running. The Security & Fire Awards for Excellence are recognized across the sector as a benchmark for outstanding performance, innovation and best practice in both security and fire. The Sustainability Champion category honors organizations that demonstrate leadership in environment...
Eversheds Sutherland has appointed partner Albert (Alby) Yuen to lead its Technology, Data and Cyber offering in Asia – the firm’s latest step in advancing its global growth strategy and underpinning its commitment to investing in exceptional talent across key markets and jurisdictions. Alby was previously Head of Technology, Media & Telecommunications (TMT) – Hong Kong, at international law firm, Linklaters where he led and developed its TMT practice, advising on major re...
Continuing its global expansion plan, and its commitment to the African continent, Integrity360 has acquired Redshift, a well-established and highly regarded cyber security services company operating out of Johannesburg in South Africa. The terms of the transaction were not disclosed. The acquisition comes on the back of Integrity360’s considerable investment in the region following the 2024 and early 2025 acquisitions of the Grove Group and Nclose. The acquisition brings Integrit...
As AI-generated phishing attacks flood inboxes with more realistic and personalized scams, DigiCert, a pioneer in intelligent trust, today released new research revealing that consumers are turning to verified brand identities in email for reassurance--especially during Cyber Week. The study, conducted by independent research firm Vitreous World, surveyed 5,000 consumers across the U.S., U.K., Australia, and New Zealand to understand how verified logos and sender authentication will...
With the new RDF6100DN dome cameras, Dallmeier is expanding its successful Domera product family. The new model series is characterized in particular by its edge analytics capability, enhanced security features and an attractive price-performance ratio. The cameras of the RDF6100DN series were specially developed for applications requiring a balance of functionality and cost-effectiveness. As a high-performance entry-level solution within the Domera product family, the cameras offer high resolu...
DigiCert, a global pioneer in intelligent trust, has been selected by Jisc, the UK’s national digital, data and technology agency for education and research, to help secure the future of the UK’s connected learning ecosystem. DigiCert will support the UK education and research community in protecting sensitive data against emerging cyber threats and building the foundations for secure collaboration and innovation. Through Jisc’s national procurement framework, member instituti...
The European Network for Cyber Security (ENCS) announces that ELES, Slovenia's transmission system operator, has joined the network as a member, reinforcing collaborative efforts to protect Europe’s electricity grid from evolving cyber threats. The partnership will give ELES access to ENCS’s collaborative threat intelligence, specialist training and technical expertise – strengthening its ability to detect, prevent and respond to cyber incidents targeting high-voltage networks...
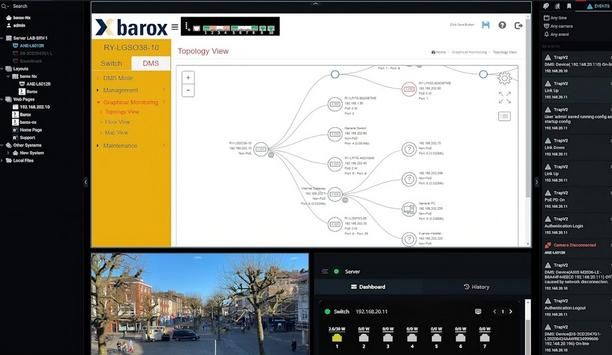
barox Kommunikation AG is delighted to announce the launch of their new technology partnership with Network Optix, the latest addition to their extensive integration portfolio with market pioneering VMS and PSIM providers. This new integration is designed to transform the management and support of Network Optix Nx Witness video networks. Utilizing the new barox Network Optix plug-in, Nx Witness users will be able to capitalize on a greater depth of integration capabilities. Key features include...
Renowned global intelligence and cyber security consultancy - S-RM has promoted Casey O’Brien to Global Head of Incident Response (IR). Casey’s appointment reflects the firm’s continued investment in its international cyber practice and its ability to support clients worldwide, around the clock. Casey will work closely with Joani Green, Chief Information Officer, to deepen collaboration between regional teams, streamline ways of working, and enhance the firm’s use of tec...
New independent research from Six Degrees, the secure, integrated cloud services provider, reveals a dangerous disconnect between retailer cyber confidence and real-world cyber resilience. Data from the Six Degrees Retail Whitepaper shows that while most UK retailers are highly confident about their security posture, one in five admit their current defenses wouldn’t prevent a cyber-attack. This disconnect has far-reaching impacts because the retail sector faces an increasing volume of att...
Google Cloud announced a significant, multi-million-dollar contract with the NATO Communication and Information Agency (NCIA) to deliver highly secure, sovereign cloud capabilities. This strategic partnership is a major step in bolstering NATO's digital infrastructure, strengthening its data governance, and enabling it to securely leverage cutting-edge cloud and AI capabilities. NCIA selected Google Distributed Cloud (GDC) to support the Joint Analysis, Training and Education Centre (JATEC). JA...
Hackuity, the risk-based vulnerability management provider, released new research revealing the mounting pressure on security teams as they struggle to keep pace with the rising number of CVEs (Common Vulnerabilities and Exposures). The Vulnerability Management Report explores the challenges of vulnerability management and includes insights from 200 IT security decision-makers across the UK and APAC. Additional strain As the number of CVEs continues to rise, nearly half (46%) of respondents s...
HID, a worldwide pioneer in trusted identity solutions, announced the appointment of Jos Beernink as Vice President Europe for its Physical Access Control (PACS) business. In this role, Beernink will lead HID’s strategy, sales and operations across the whole European region, helping organizations leverage trusted identity and access control technologies to create a secure, smarter and more efficient workplace and physical spaces. Prior roles of Beernink Beernink brings more than 2...
HID, a pioneer in trusted identity solutions, has achieved Texas Risk and Authorization Management Program (TX-RAMP) certification for its Public Key Infrastructure as a Service (PKIaaS) solution. This certification demonstrates HID’s commitment to cybersecurity excellence and enables Texas state and local government to confidently engage with approved, trusted providers to procure secure, cloud-based certificate lifecycle management services with faster timelines and reduced administrati...
Businesses have come a long way in terms of security measures, evolving from a simple lock and key to sophisticated digital systems. In the past, ensuring a secure premise was all about hiring guards, installing CCTV cameras, and ensuring gates were locked. Now, the landscape of business protection has changed, and with it has come the necessity for commercial establishments to adapt swiftly. Why modern security matters The contemporary business landscape is an intricate web of both offline a...
As the anticipated “Q-Day” approaches—the moment when quantum computers will render traditional encryption obsolete—executives are beginning to recognize that quantum risk management has evolved into a shared value-chain imperative, not a narrow cybersecurity exercise within individual organizations. The ability to withstand quantum-driven disruption now depends on how effectively corporate ecosystems—spanning suppliers, customers, platforms, and partners—coor...
Suprema, a global pioneer of AI-powered security solutions, has been recognized by A&S magazine as a ‘2025 Global Top 50 Security Company’, marking its fifteenth consecutive year on the prestigious list. This consistent achievement underscores the company’s sustained growth, innovation, and global influence. A&S ranks the world’s top security companies annually based on revenue and profitability. Suprema has secured its place on this list since 2011. asmag.com&r...
Immersive, the pioneer in cyber resilience, announced the general availability of Dynamic Threat Range, a groundbreaking new capability within its Immersive One platform that transforms how organizations validate and improve cyber readiness. Dynamic Threat Range runs authentic, full-chain live-fire attacks within supported enterprise environments, delivering a level of realism that traditional log replays cannot match. Powered by a new Infrastructure-as-Code foundation, it enables complex, real...
42Crunch, the pioneer in DevSecOps for API security, announced that its freely available API security testing tools for developers—integrated directly into popular IDEs including VS Code, JetBrains, and Eclipse—has surpassed the 2 million downloads worldwide. This milestone reflects the accelerating demand from CISOs for enterprises to adopt a proactive approach to API security. As AI workloads multiply and organizations rely more heavily on automated systems that consume vast numbe...
SoSafe, Europe's pioneer in security awareness training and human risk management, announced the appointment of Daniel Farkas as Chief Revenue Officer (CRO) effective immediately and Peter Grausgruber as Chief Financial Officer (CFO) effective 1 January 2026. The new hires join the executive leadership team as the company enters its next phase of growth and scale. As CRO, Daniel Farkas will lead all revenue-generating functions, including sales, partnerships, marketing, and customer succes...
Zimperium, the global pioneer in mobile security, revealed findings from its zLabs team showing that thousands of popular Android applications — including top travel, airline, and weather apps — are still using an outdated mapping component that could put users and enterprises at risk. The investigation, titled “Follow the Map to Enterprise Risk: What’s Inside Popular Android Apps,” found that a legacy library known as libmapbox-gl.so, once part of Mapbox GL Native...
Tokio Marine Kiln (TMK), a pioneering specialist insurer, announces the appointment of Cesar Silvestre as Head of Cyber Reinsurance Solutions, reporting to Laila Khudairi, Head of Cyber & Enterprise Risk. He takes up his new role with immediate effect and will lead the launch of TMK's new cyber reinsurance solutions offering. Silvestre brings over 12 years of specialized insurance experience to his new role. He joins from Beazley where he served as a Specialty Treaty Underwriter in the pro...
Entrust, a global pioneer in identity-centric security solutions, released its seventh annual Identity Fraud Report for 2026. The report examines global trends, tactics, and techniques used in identity fraud over the past year, providing actionable insights to help businesses protect their customers and operations. Deepfakes and injection attacks on the rise New data reveals deepfakes account for one in five biometric fraud attempts, and instances of deepfaked selfies...
Eviden, the Atos Group product brand pioneering in advanced computing, announces the rankings of its 58 Eviden-built systems in the TOP500 and Green500, official listings of the world’s most powerful and most energy-efficient supercomputers. Amongst the 58 Eviden-built systems listed in the TOP500, JUPITER, through its Booster partition, remains the 4th most powerful supercomputer in the world and Europe’s 1st, marking a historic milestone as Europe’s first system to officiall...
As agentic commerce takes hold, retailers are entering a new phase of automation, where AI agents act on behalf of real users to browse, compare, and buy. But these same capabilities can be weaponized by fraudsters. This Black Friday, the challenge isn’t stopping bots; it’s distinguishing between legitimate agent-driven interactions and malicious automation designed to mimic them. Identity amid rising automation That distinction matters most at the account layer, where retailers m...
Eviden, the Atos Group product brand pioneering in advanced computing, and AMD announced their selection to build Alice Recoque, a next-generation supercomputer to support the need for scientific computing (HPC) and artificial intelligence (AI), serving as an AI Factory. Alice Recoque will be France’s first and Europe’s second Exascale supercomputer, a machine to expand Europe’s AI and research capabilities while ensuring energy efficiency and sovereignty. This project, led b...
FireMon, the pioneering network security and firewall policy management company, detailed expanded support for Zero Trust microsegmentation across hybrid environments, including a deeper integration with Illumio and continued coverage for VMware NSX and Zscaler. By normalizing, analyzing, and continuously validating segmentation intent across network, virtual, and host enforcement points, FireMon helps security teams operationalize Zero Trust at enterprise scale. Firewall governance...
Claroty, the cyber-physical systems (CPS) protection company, launched The CPS Library across its market-pioneering Claroty xDome and Claroty Continuous Threat Detection (CTD) solutions. The CPS Library is the industry’s only asset catalog that reaches new depths of visibility and enables precise and deterministic traceability for vulnerability attribution. To build the AI-powered, first-of-its-kind repository, Claroty partnered with automation vendors and medical device manufacturers, i...
Cyber threats against the Office for Budget Responsibility have over doubled in the past 12 months, ahead of Rachel Reeves’ crunch Autumn Budget. On November 26th, Reeves is set to announce a wave of economic policies to fight against the high cost of borrowing in the UK, with hints of income tax and inheritance tax hikes on the horizon. The Office for Budget Responsibility provides an independent analysis of the UK’s public finances, from which the Chancellor of the Exchequ...